Federal Information Security Management Act of 2002 (FISMA) requires Federal Agencies to implement formal security plans and comply with security guidance defined by the National Institute of Standards and Technology.
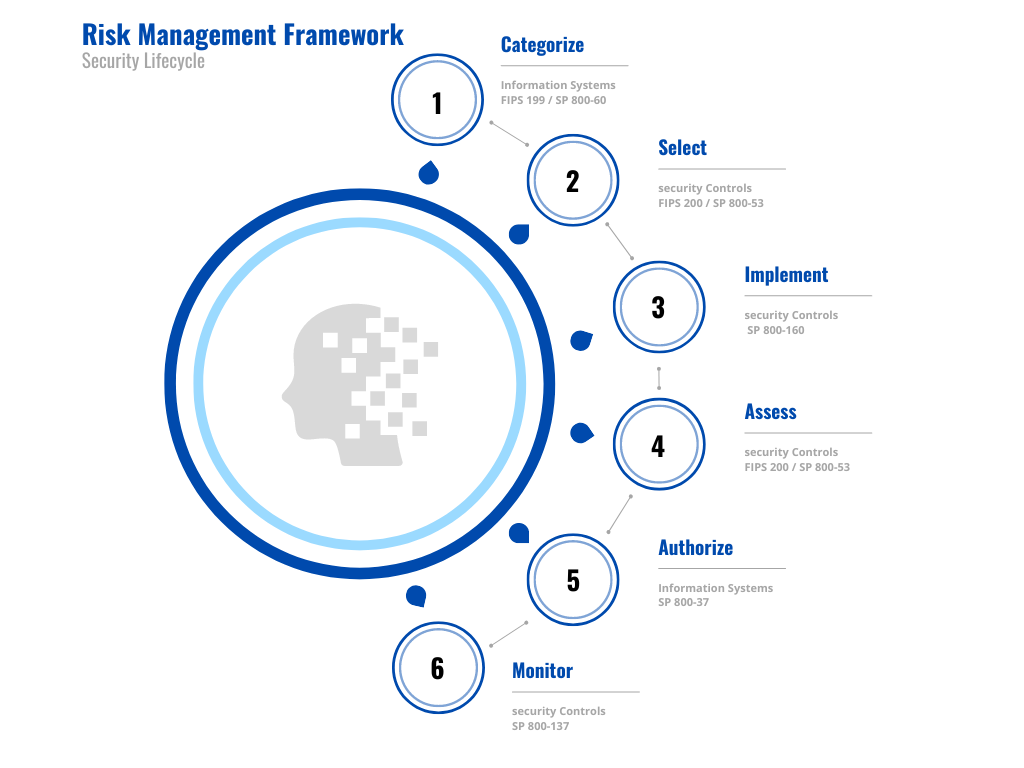
NIST outlines a 6 step process for FISMA compliance:
(Click to enlarge)
At the highest level FISMA requires agencies to:
- Agencies to maintain an up-to-date inventory
- Categorize systems and data based on risk
- Create and maintain a system security plan
- Implement security controls
- Receive and maintain Certification & Accreditation
- Continuously monitor systems
How we can help
Consulting
A large part of ensuring an ATO is received and maintained involves the development and update of all required security documentation. There are numerous things to consider that can materially affect A&A documentation: common controls, hybrid controls, major system changes, compensating controls, risk waivers, risk acceptances, etc. Inadequate documentation is the number one reason why the issuances of ATOs are delayed. GAI Cyber has substantial expertise in navigating the pitfalls involved with the ATO process and streamlining security artifact creation. Our team will develop and update all required documents for a new or ongoing FISMA security authorization for FISMA, including:
- System Security Plan (SSP)
- Federal Information Processing Standard Publication 199 (FIPS 199) Categorization
- Incident Response Plan (IRP)
- Contingency Plan (CP)
- Disaster Recovery Plan (DRP)
- Privacy Threshold Analysis (PTA)
- Privacy Impact Assessment (PIA)
- Configuration Management Plan (CMP)
- Policies and Procedures
Assessment
A crucial part of FISMA compliance is procuring an independent third-party assessor to audit the state of your compliance. Our team will conduct all required assessment procedures with your organization to give you an accurate snapshot of the current state of your security program and FISMA compliance.
We offer two types of Assessments:
Readiness Assessment
A tailored assessment that is scoped based on your needs that will identify a list of gaps for you to remediate prior to undergoing a formal audit.
Independent 3rd Party Assessment
An unbiased assessment of your compliance against required NIST 800-53 controls. Our team will interview personnel, examine documentation, and conduct technical testing in order to validate compliance and will notate deficiencies. This type of assessment is what is required for an Agency to grant an Authority to Operate (ATO). Our assessment process flow is described below.
Contact a Cybersecurity Expert.
Are you ready to start your compliance journey? GAI Cyber is ready to assist with any of your compliance, cybersecurity, and privacy needs.
GAI Compliance Solutions.
Vulnerability Scanning
Identify. Investigate. Remediate.