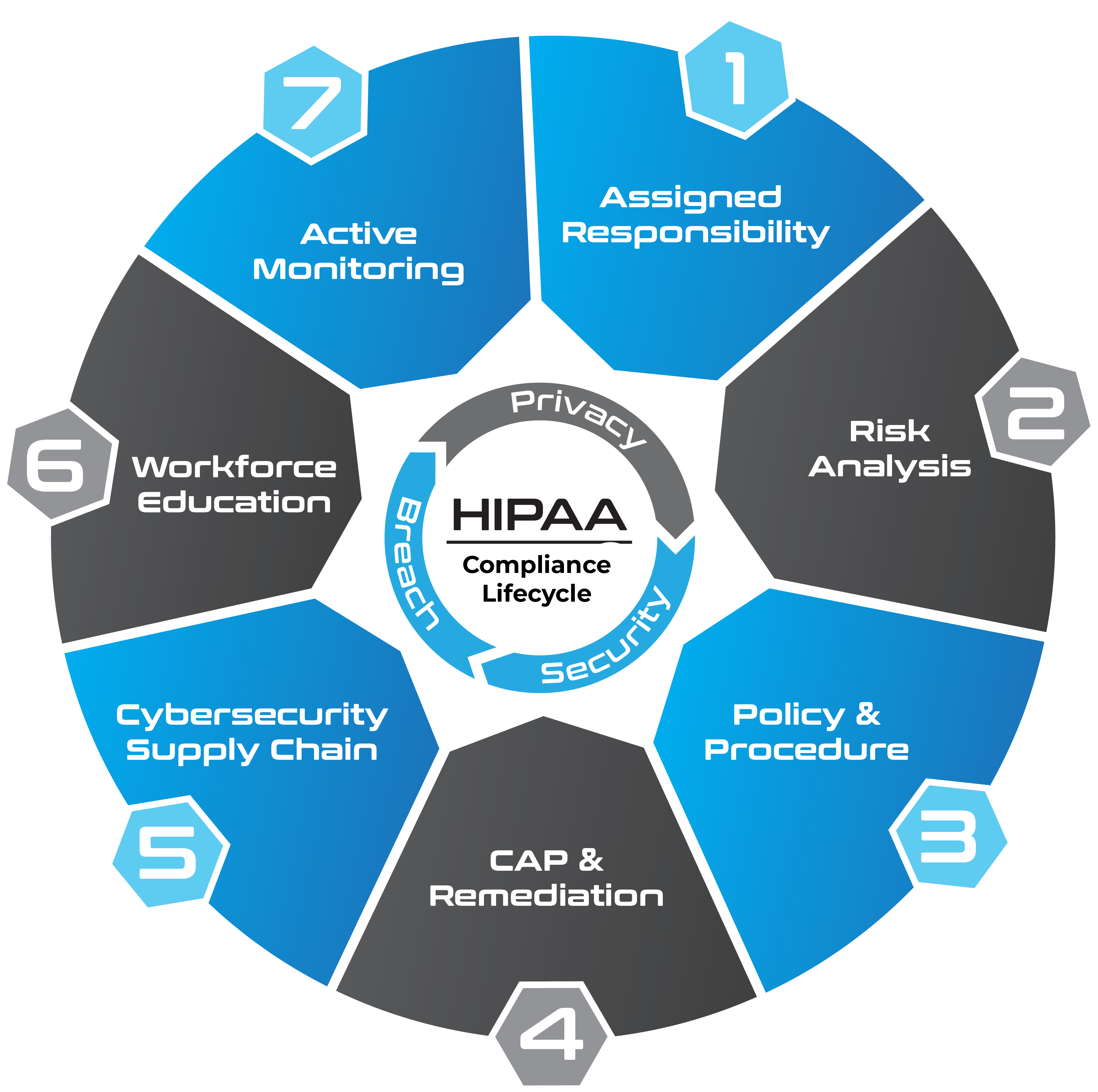
The Health Insurance Portability and Accountability Act of 1996 (HIPPA) outlines the legal requirements regarding the use and disclosure of protected health information (PHI).
HIPPA defines two groups of organizations that need to be compliant:
Covered Entities: Any organization that directly collects, creates, or transmits electronic PHI. Most commonly: health care providers and health insurance providers.
Business Associates: Any organization that encounters PHI over the course of work they have been contracted to perform by a covered entity. This often manifests as a business associate storing, processing or transmitting PHI on behalf of a covered entity. Common business associates include: third party service providers, independent consultants, hosting companies, and attorneys.
HIPPA has defined various rules that Covered Entities and Business Associates must adhere to:
Privacy Rule: Only applies to Covered Entities and defines patients’ right to PHI.
Security Rule: Applies to both Covered Entities and Business Associates and outlines security safeguards, policies and procedures that must be implemented.
Breach Notification Rule: Applies to both Covered Entities and Business Associates and defines breach notification requirements depending on the size and scope of a breach.
Omnibus Rule: An addendum to HIPPA, it requires that mandates all business associates must be HIPPA compliant and requires Business Associated Agreements must be in place between a covered entity and a business associate prior to the sharing or transfer of PHI.
The GAI Cyber team has substantial expertise in navigating the various pitfalls surround HIPPA compliance. The most perilous of which is often inevitable: data breaches. Our team will assess your current security posture and existing compliance with HIPPA and tailor a roadmap that minimizes your risk surface to non-compliancy threats and risks.
Contact a Cybersecurity Expert.
Are you ready to start your compliance journey? GAI Cyber is ready to assist with any of your compliance, cybersecurity, and privacy needs.
GAI Compliance Solutions.
Vulnerability Scanning
Identify. Investigate. Remediate.