About Vulnerability Scanning
The most efficient way to get breadth of coverage in the identification of vulnerabilities is through security scanning. Vulnerability scanners leverage a database of checks that run against devices on the network to determine patch levels, configuration settings, and susceptibility to different vectors of attack.
We work with our clients to understand the impact of identified vulnerabilities by considering the: nature of the vulnerability, likelihood of exploitation, asset criticality, location of the asset, and severity of the risk if the vulnerability were to be exploited. We then take these factors into account in order to determine the true level of risk a vulnerability poses to your organization.
GAI Cyber offers a wide range of vulnerability scanning products and services to easily and effectively manage scanning requirements. Our scanning tools include coverage for most any device with an IP address, including scanning capability for: Dynamic Application, Static Code, Network Infrastructure, Databases and Mobile Devices. We only leverage the best industry standard tools, including: Nmap, Tenable Nessus, Appscan, Webinspect, Qualys, Netsparker, Kali Linux, Checkmarx, Burp Suite, Accunetix, Fortify.
Prior to conducting any vulnerability scanning we ensure your inventory is up-to-date by running discovery scans across network subnets. Once inventory is validated, we work with your team to determine the most efficient way to conduct scanning to meet your requirements, minimize operational disruption and achieve your security posture goals. We also have targeted discussions around sensitive or critical assets that need to be handled differently during the scanning process.
Why GAI Cyber Solutions
GAI Compliance Solutions.
Vulnerability Scanning
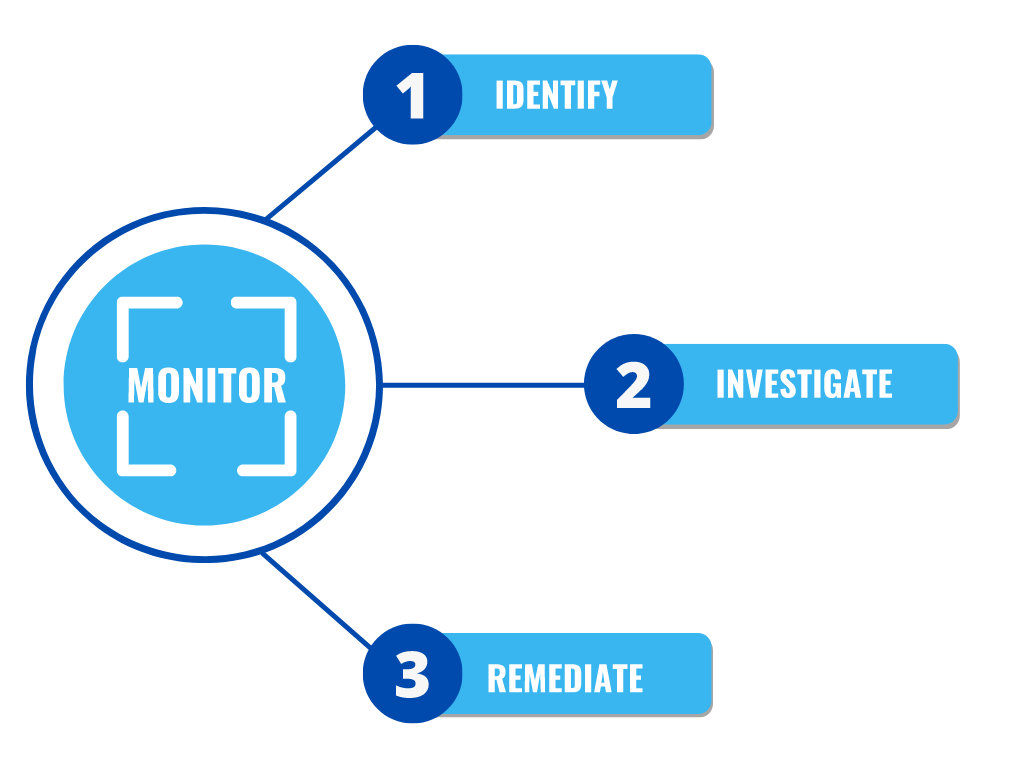
Identify. Investigate. Remediate.